Make sure Nexus Repository has been setup with Self Signed certificate, certificate for host/server e.g. “silencer.bigpond”.
The following instructions have been successfully tested in Nexus version 3.2.0-01.
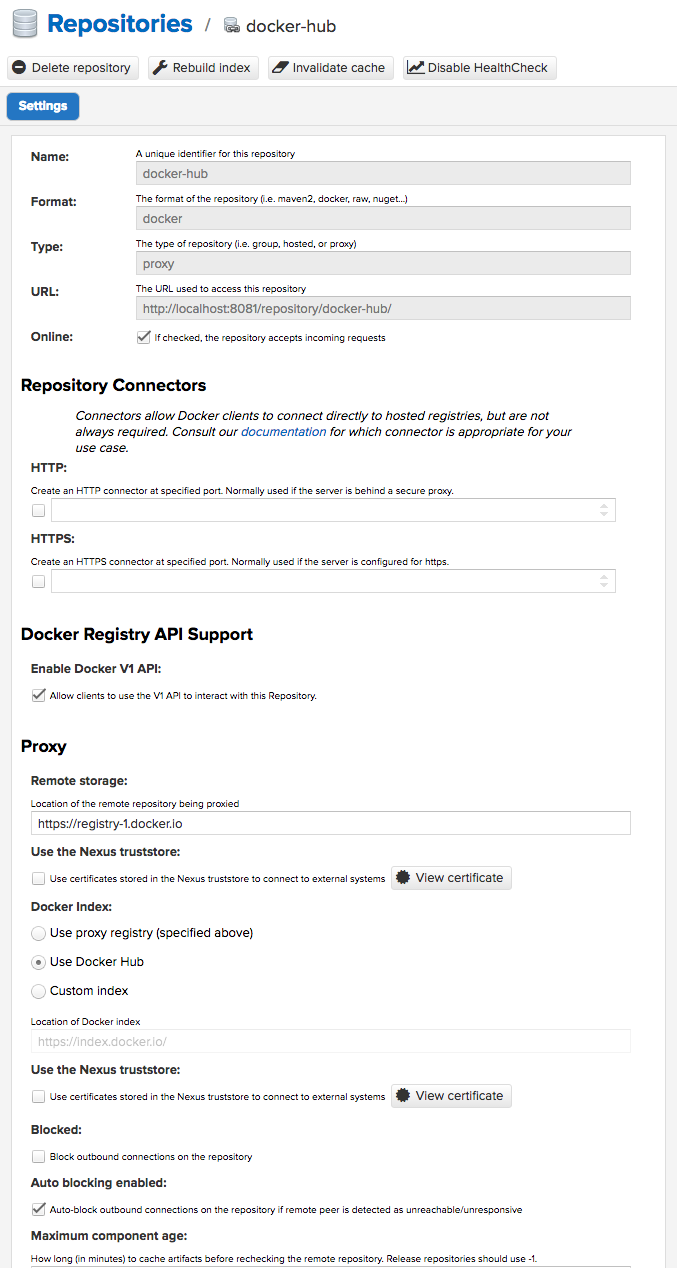
Create Docker Hub repository in Nexus
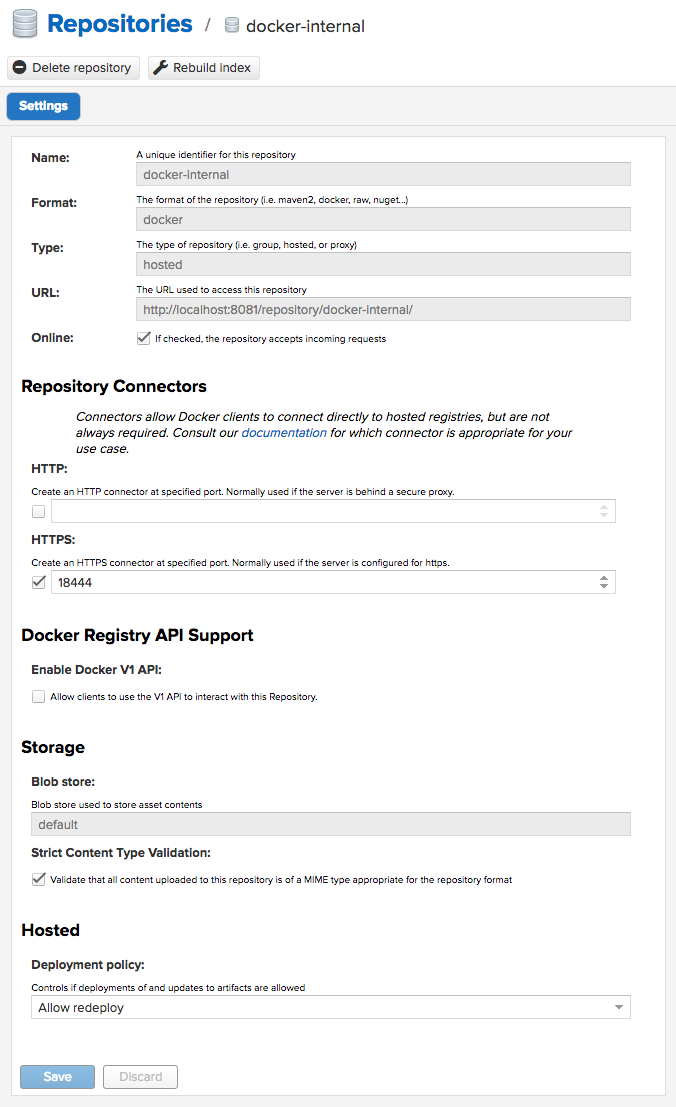
Create Docker Internal repository in Nexus
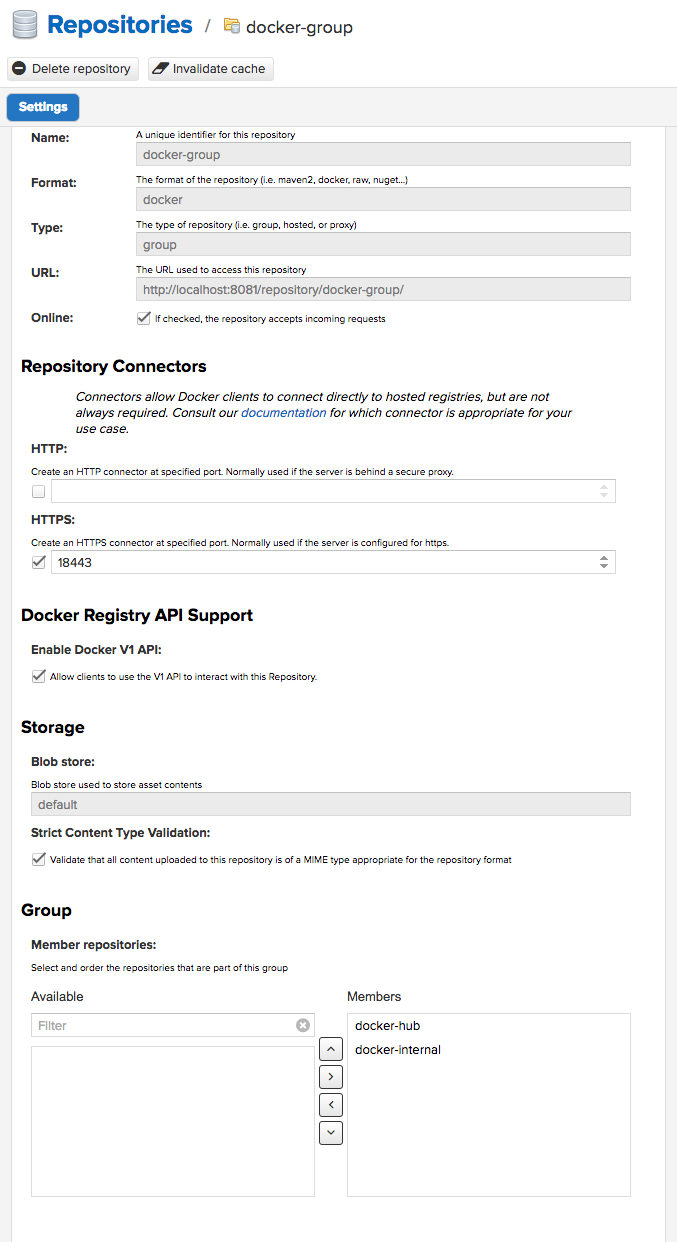
Create Docker Group repository in Nexus
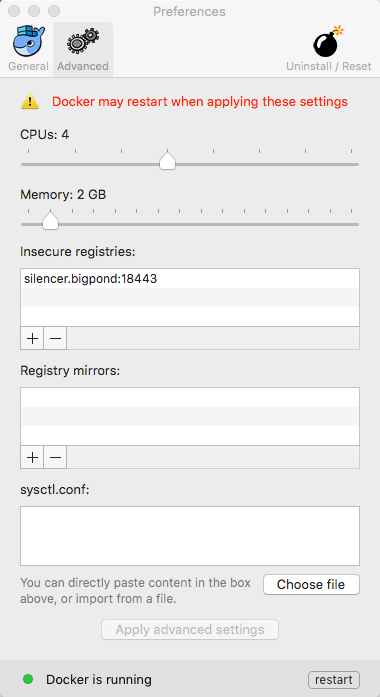
Run Docker with Docker Native
Add Docker Private Registry in Insecure Registries
Now this approach supports docker pull and docker push.
Work around with “x509: certificate signed by unknown authority“ error by adding “–disable-content-trust” option on docker push command line if Docker doesn’t accept Self-Signed certificate.
Add Docker Private Registry server’s certificate into Docker Virtual Machine CA list
1 | 𝜆 keytool -printcert -rfc -sslserver silencer.bigpond:8444 > silencer.bigpond.pem |
1 | 𝜆 screen ~/Library/Containers/com.docker.docker/Data/com.docker.driver.amd64-linux/tty |
Inside Docker Virtual Machine, follow these steps:
1 | $ sudo cat silencer.bigpond.pem >> /etc/ssl/certs/ca-certificates.crt |
With Docker Toolbox
Add Docker Private Registry server’s certificate into Docker Virtual Machine CA list
1 | 𝜆 keytool -printcert -rfc -sslserver silencer.bigpond:8444 > silencer.bigpond.pem |
Inside Docker Virtual Machine, follow these steps:
1 | $ sudo cat silencer.bigpond.pem >> /etc/ssl/certs/ca-certificates.crt |
Press Ctrl + D and Ctrl + D to exist SCREEN program. Type “screen -r” to re-entry SCREEN program.
Additional Certificates
Download 3rd party Repository server’s certificate. Use tool like KeyStore Explorer to add 3rd party server certificates into existing keystore.jks. Due to a certificate chain that does not exist within the existing Java truststore, Java does not trust the certificate and fails to connect to the application.
Test
1 | 𝜆 docker login silencer.bigpond:18443 |
1 | 𝜆 docker search silencer.bigpond:18443/tomcat |
1 | 𝜆 docker login silencer.bigpond:18444 |
1 | 𝜆 docker build -t jtech/camel-spring:latest . |
1 | 𝜆 docker push --disable-content-trust silencer.bigpond:18444/jtech/camel-spring:latest |
Note
- Due to Docker Virtual Machine is immutable, the CA certificate added change made inside VM is ephemeral, and lost after VM is restarted
- Docker Private Registry ONLY supports HTTPS, NOT HTTP
- Nexus repository MUST register and use server certificate for host e.g. “silencer.bigpond”, NOT “localhost.bigpond” to run Docker Private Registry
- Try with “–disable-content-trust” if error like “Get https://silencer.gateway:18444/v1/_ping: x509: certificate signed by unknown authority”
Reference
- Private Registry for Docker, https://books.sonatype.com/nexus-book/3.0/reference/docker.html
- Using Self-Signed Certificates with Nexus Repository Manager and Docker Daemon, https://support.sonatype.com/hc/en-us/articles/217542177
- SSL Certificate Guide, https://support.sonatype.com/hc/en-us/articles/213465768
- Setup HTTPS access Nexus Repository, https://github.com/TerrenceMiao/nexus/wiki/Setup-HTTPS-access-Nexus-Repository-Manager-OSS-3.xx
- Add Self Signed CA certificate into Docker’s CA list, https://github.com/klippx/inject-docker-certs
- Adding Self Signed certificate in Docker Native for Mac, https://forums.docker.com/t/adding-self-signed-certificates/9761